Looking for a solution to the following issues?
Lack of IT engineers well-versed in security measures
Need to ensure the full implementation of cybersecurity measures
Need to know whether current cybersecurity measures are appropriate
Need to ensure security measures suitable for remote work
Having been pointed out by business partners to enhance security measures
Want to automate security measures where possible
Service overview
Security and Security Consulting is a service to provide everything from consulting to the continuous assistance for the series of processes related to security, including requirement definition, planning, construction, implementation, auditing/inspection, evaluation/analysis, and improvement.
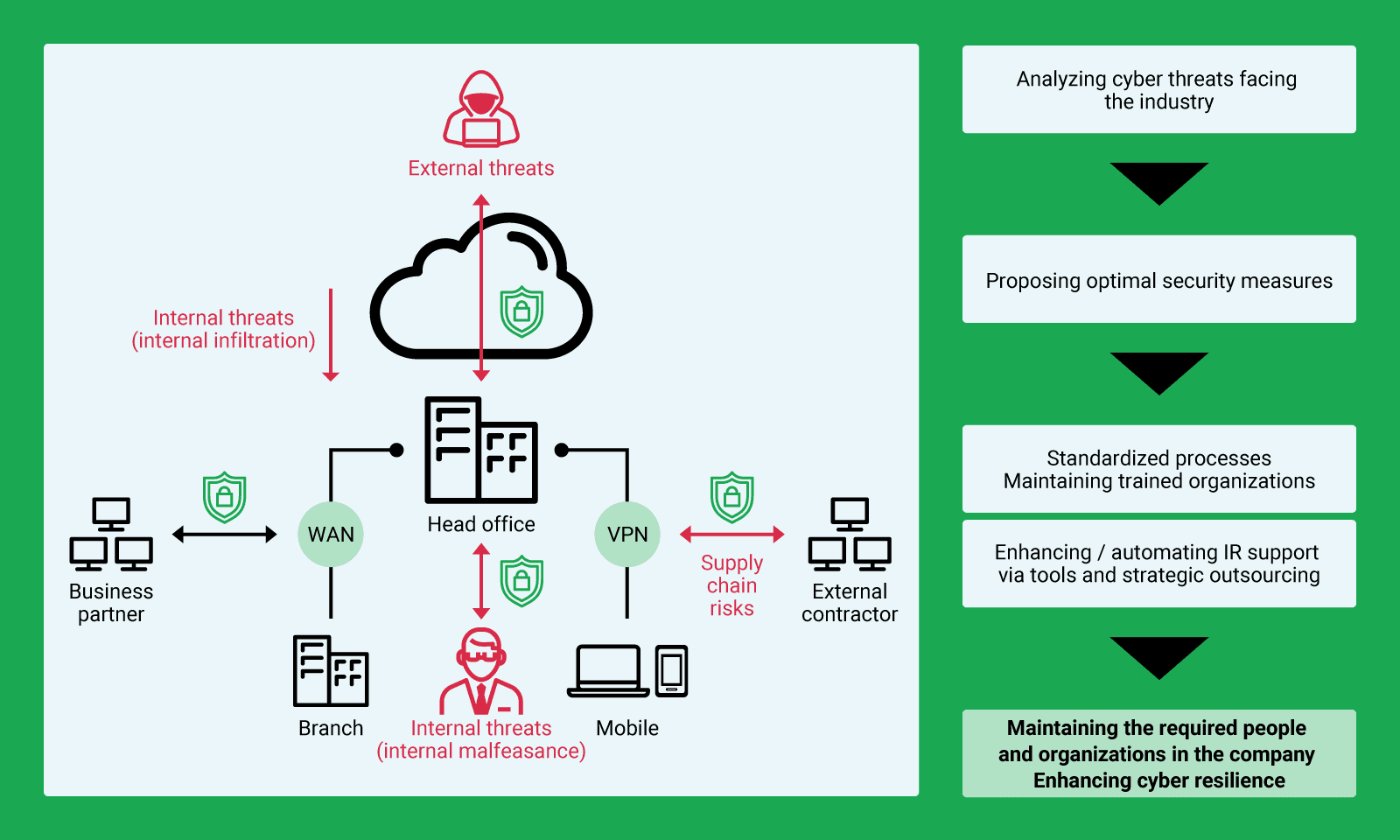
We protect the customer's IT environment from cybersecurity threats becoming more sophisticated nowadays.
Service features
Risk assessment
We analyze and evaluate the current measures based on the customer’s internal policy, products used, and the situation of operation.
Presenting the direction of suitable security measures
We analyze cyber threats facing the industry and propose optimal security measures to the customer.
Roadmap formulation
We take into consideration the priority of security measures focused on the customer’s environment to create a roadmap for the implementation.
A 50-year track record of protecting critical infrastructure
We propose optimal security measures based on our 50 years of experience in protecting critical infrastructure such as financial institutions.
On-site experience and knowledge based proposal
We identify customer’s needs to provide on-target proposals and optimal security services based on on-site information and track record.
Adaptable to cutting-edge solutions
We provide security measures focused not only on basic security but also cutting-edge technology such as AI and OT.
List of provided services
Security planning
Cybersecurity/assessment roadmap formulation service (for IT/control)
Information security/assessment roadmap formulation service
Simple packet survey service (for IT/control)
Security measures
CSIRT consulting
Consulting for security policy/regulation formulation
Cybersecurity/incident response education/training service
Security education service (content creation, etc.)
Security environment construction
Security product adoption assistance/construction service
Security inspection
Targeted attack e-mail training service
Vulnerability diagnosis service (for IT/control)
Cloud vulnerability diagnosis service (for AWS)
Information security audit service
Security environment improvement
Security advisory service
(providing security information topics, advice, and cyber insurance)
Risk assessment
Data center locations
Applicable laws and jurisdiction for disputes
Data encryption/encryption key user management
Web interface authentication method for administrators
Feasibility of audit implementation
